PrimeFactors
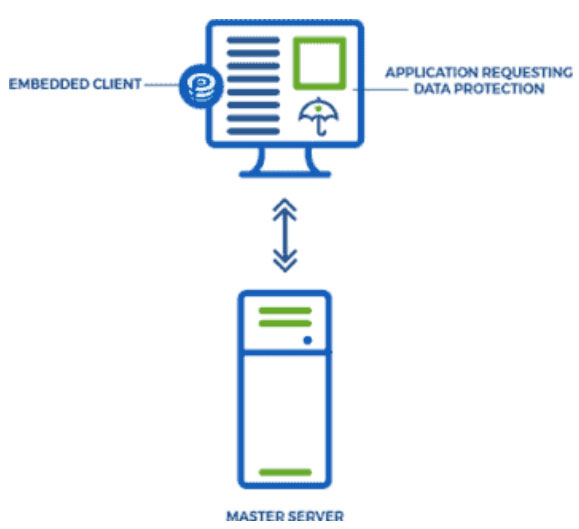
EncryptRIGHT has a modular Client/Server architecture designed for scalability and resiliency to meet the data protection needs of any sized enterprise. EncryptRIGHT clients, installed throughout the enterprise and cloud, support most cryptographic functions of EncryptRIGHT locally. EncryptRIGHT data protection policies (DPP) are centrally defined in the Master Server and rolled out to each additional server and client across the enterprise and cloud, ensuring that each function of data protection is executed in accordance with its up-to-date policy.
Designed for Compatibility
With out-of-the-box compatibility with IBM Mainframe (z/OS), IBM i (OS/400), Linux (RHEL), Solaris (SPARC), IBM AIX, and Windows, EncryptRIGHT is designed to deploy quickly wherever applications reside, without complex customization.
Designed for Scalability
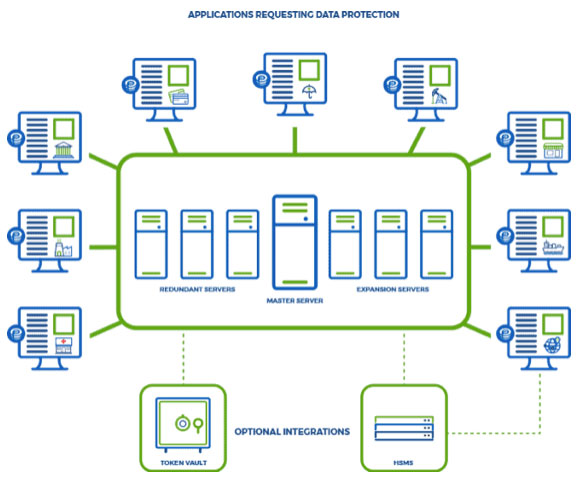
Additional EncryptRIGHT® servers can be deployed to share the processing workload with the Master Server and for redundancy should any server fail. These servers can also assist in rolling out policies to EncryptRIGHT clients. Redundant Master Servers synchronize all of the definitions and logic of EncryptRIGHT Master Server and can be promoted to become Master Server, should the Master Server fail.
EncryptRIGHT includes flexible audit logging and reporting functionality to support traceability, alerting and compliance for visible data protection.
Strong encryption is the last line of defense in data protection. EncryptRIGHT software delivers strong data security with a primary focus on application level data encryption, and also supports encrypting databases with transparent data base encryption (TDE) and encrypting files for transfer or backup, protecting sensitive data regardless of where it is used, moved or stored.
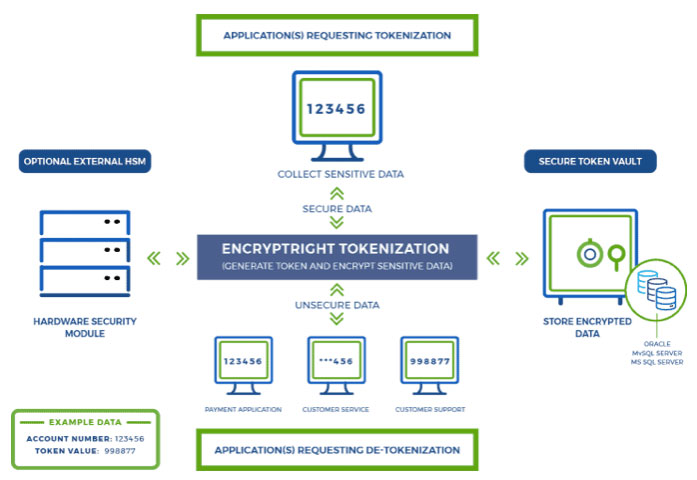
The EncryptRIGHT® Tokenization software solution offers robust data protection functionality for pseudonymization and anonymization of sensitive data by substituting surrogate data elements in place of Personally Identifiable Information (PII) and other sensitive data — that is, to replace things like credit card numbers, Social Security numbers, healthcare data, and other sensitive information with surrogate “tokens”. The tokens, not the original sensitive information, can be used by and shared with the various systems, applications or sites that may need access to the information, while the original data remains secured and contained.
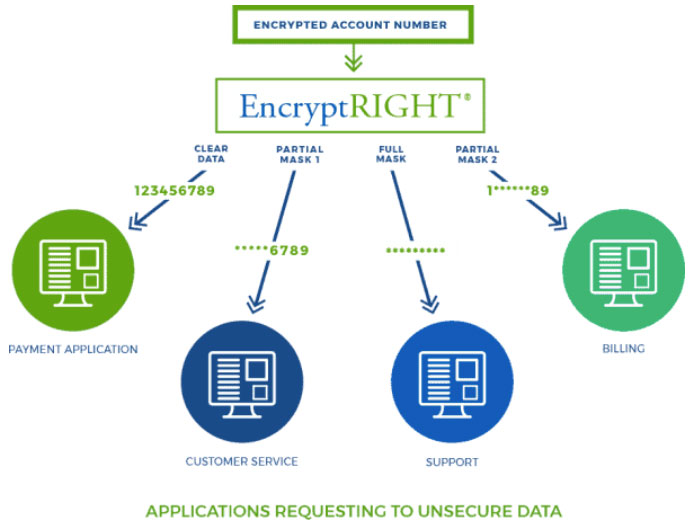
EncryptRIGHT can apply data masks to uniquely obscure parts of a piece of data in the manner appropriate for each user who is authorized to access and unsecure sensitive data to enforce appropriate data privacy.
Comprehensive data protection is more than just algorithms and keys, it is also about defining and enforcing data access controls. EncryptRIGHT leverages strong role-based access controls to define who has access to sensitive data, assign appropriate data access permissions and easily orchestrate unlocking the protected data in a need-to-know manner – allowing each user to access data only to the extent to which they are authorized. This is a key component to the data security governance approach to protecting data.
Data access controls start with defining users and permissions. In EncryptRIGHT, users and logical user groups can be defined and assigned unique permissions. Since every function of EncryptRIGHT, requires a valid User ID and password, role-based data access controls can be applied in real time to authorize user access to a specific function. This is integral to data masking and managing data privacy.
Encryption Key Management
EncryptRIGHT includes a comprehensive, centralized encryption key management system for orchestrating all cryptographic keys related to data protection, including the ability to generate, exchange, distribute, store, rotate, temporarily suspend, revoke, and destroy cryptographic keys for all of the data EncryptRIGHT touches.